Door control system: Difference between revisions
m (→Glados Voice) |
|||
| Line 66: | Line 66: | ||
Tom and I have looked for a vocoder or similar in Audacity that will do this for you. I'll make a video of this and stick it on YouTube at some point. Believe it or not, it is faster than the website as this is exactly what that website in the links is doing. | Tom and I have looked for a vocoder or similar in Audacity that will do this for you. I'll make a video of this and stick it on YouTube at some point. Believe it or not, it is faster than the website as this is exactly what that website in the links is doing. | ||
I'll see about implementing the processing algorithm in ChucK so it can be a command-line operation the next time I'm prototyping some FFT analysis stuff with it. -- [[User:Anthony|Anthony]] | |||
=== Bell's IP === | === Bell's IP === | ||
Revision as of 01:55, 20 February 2011
Preface
The major difference between a thing that might go wrong and a thing that cannot possibly go wrong is that when a thing that cannot possibly go wrong goes wrong it usually turns out to be impossible to get at or repair.
Overview
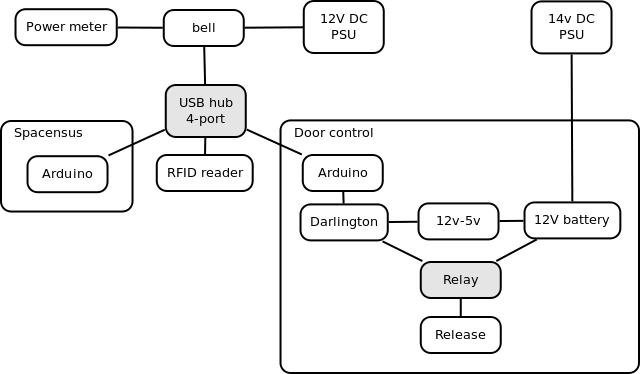
We have a Tikitag RFID reader, embedded in the door, which we use to automatically open the door when authenticated.
Details
The software runs on Flowers, and its code is on Github.
The access list is currently a text file, copied via a script from Flowers. The text file simply consists of card ID and name.
The door opener connects to robonaut on Babbage to announce whenever the door is opened, and also flashes the lights on using Lighted, also on Babbage.
The announcement uses the GLaDOS voice. You can generate your own name file using this generator and place it into the appropriate directory on Flowers. Although you can use that page, a better solution is presented below.
Adding a card
Connect to Flowers, gain root.
Then:
root@flowers:~$ screen -dr doorbot
You will see the log of attempted access. Press Ctrl+A Ctrl+D to disconnect and add the card manually to Doorbot/cardtable.dat.
Override
Please use this with caution. Once unlocked, the door must be physically opened and closed again to relock.
ssh root@flowers Doorbot/openDoor.py
The password is hackspace. If the arduino has somehow changed port, you might need to edit that in openDoor.py
- If this ambiguity becomes a problem (eg if another serial port is added), update the udev rules : debian distributions create /dev/serial/by-id where the links in that directory include in their names the unique serial number assigned to the FTDI chip on the arduino board.
- This will happen when I/someone gets around to it :D Ms7821 08:38, 27 August 2010 (UTC)
If you unlock the door remotely, use the door webcam to check someone has entered the space.
Logging & maintenance
If you make changes or discover a problem with doorbot, please add it to the logbook.
- The main script is rundoorbot, which announces to irccat on Babbage if the python script dies.
- The python script (doorbot.py) announces on successful initialisation.
- A separate script, rootfswd, announces and reboots the machine if the USB drive is disconnected.
The service currently runs in screen, to avoid any disk syncing issues. To view it, use screen -dr doorbot. Note that killing the python script with Ctrl+C will be announced. To start or stop doorbot without connecting to screen, use:
/etc/init.d/doorbot start /etc/init.d/doorbot stop
Glados Voice
The Glados voices were generated by oni following the method found by Tom Wyatt. To create a glados voice one must do the following:
- Go to ATandT's Text to Speech page. Type in your name and download the file
- Load up the program Melodyne
- Select the entire Waveform
- Using the melodic algorithm, double click on one section of the waveform. I believe this moves the form to its nearest notes.
- Using the zig Zag looking tool, flatten the pitch.
- Up the pitch by dragging upwards by 160 or so.
- Save
Tom and I have looked for a vocoder or similar in Audacity that will do this for you. I'll make a video of this and stick it on YouTube at some point. Believe it or not, it is faster than the website as this is exactly what that website in the links is doing.
I'll see about implementing the processing algorithm in ChucK so it can be a command-line operation the next time I'm prototyping some FFT analysis stuff with it. -- Anthony
Bell's IP
172.31.24.197
Flowers's IP
172.31.24.161