Door control system: Difference between revisions
m (→Adding a card: RFID notes) |
(recent oyster cards may not be designed for continuous power draw?) |
||
| (65 intermediate revisions by 8 users not shown) | |||
| Line 3: | Line 3: | ||
<blockquote>The major difference between a thing that might go wrong and a thing that cannot possibly go wrong is that when a thing that cannot possibly go wrong goes wrong it usually turns out to be impossible to get at or repair.</blockquote> ''- Douglas Adams, 'Mostly Harmless''' | <blockquote>The major difference between a thing that might go wrong and a thing that cannot possibly go wrong is that when a thing that cannot possibly go wrong goes wrong it usually turns out to be impossible to get at or repair.</blockquote> ''- Douglas Adams, 'Mostly Harmless''' | ||
== Adding a card== | |||
If you're a new or pending member and looking to add a card to enter the space on your own, be sure you have an [https://simple.wikipedia.org/wiki/RFID RFID or Contactless Smart] Card that operates on the 13.56MHz frequency. You likely have several in your wallet and may not even know it. Note that our doorbot RFID readers do NOT read the older 125kHz frequency RFID cards frequently used for older 1990s/early 2000s era office/housing access, so not every card works in our system. You are likely in luck and have at least one 13.56MHz card already: the [https://en.wikipedia.org/wiki/Oyster_card#Technology Transport for London Oyster card] is by far the most popular card used by LHS members, but several members have also successfully used various hotel RFID keycards, contactless credit and debit cards, some RFID wristbands, and some compatible government ID cards as well. | |||
=== Cards that are known to work well, in decreasing order of goodness === | |||
* [https://secure.tesco.com/account/en-GB/register-clubcard Tesco Clubcard (full-sized credit-card form factor has RFID)] - Free Sign-up | |||
* EV charging membership cards (Source London, Polar, GeniePoint etc) | |||
* BMW DriveNow membership cards | |||
* [https://www.richmond.gov.uk/richmondcard Richmond Card for Parking Library Leisure Services in the London Borough of Richmond-upon-Thames] - Free Sign-up for LBRUT residents | |||
* Premier Inn keycards that you forgot to hand back on checkout. | |||
* [https://oyster.tfl.gov.uk/oyster/link/0005.do Transport for London Oyster cards] - reports that some recent Oyster cards may draw more power for continuous reads. | |||
=== Cards that don't work as well === | |||
* Contactless bank cards have more processing power on-board, and need quite a lot of RF energy to activate, so may not work as reliably as simpler cards like Oyster card or simple keyfobs. We have refitted all readers known to have problems activating bank cards with more reliable readers. Don't worry, we don't have the decryption keys to do anything banking related with your bank card, we just read the serial number, not the number printed on the front. (See below about Monzo and N26 payment cards, which have their own quirks) | |||
* Passports with RFID chips will not work, and by attempting to use them will reset some internal read count in the passport, which may raise questions at border crossings. | |||
* Some contactless bank cards are shipped to the recipient with the NFC functionality entirely disabled until the cardholder performs a valid chip-and-pin transaction. | |||
* TO BE CLEAR, THESE KINDS OF CARDS ARE NOT RECOMMENDED. PLEASE DO NOT USE & PLEASE DO NOT COMPLAIN IF YOU EXPERIENCE ISSUES - ALL BETS ARE OFF ;) | |||
=== 'Cards' that don't work at all === | |||
* Apple Pay | |||
* Android Pay | |||
* Most Android card-simulator apps | |||
* New (August 2019) Monzo payment cards | |||
* The new "N26" Bank contactless card | |||
All of these generate a random UID for each transaction. | |||
* 125kHz frequency RFID cards (HID building entry systems) | |||
If you still cannot find a capable card, you can buy them relatively easy off of [https://www.ebay.co.uk/sch/i.html?_nkw=rfid+13.56mhz eBay] or [https://smile.amazon.co.uk/s/ref=nb_sb_noss_1?url=search-alias%3Daps&field-keywords=13.56mhz Amazon UK] or a local vendor such as [https://coolcomponents.co.uk/products/rfid-tag-card-dual-125khz-13-56mhz-mifare-4k Cool Components] | |||
=== Adding membership card remotely === | |||
A card can be linked to a membership account remotely, without going into the Hackspace. It's convenient for first-time access or in case you forget your card at home. Any of the cards listed in the section [[Door control system#Cards that are known to work well|Cards that are known to work well]] should work. All you need is an NFC card reader, such as an Android phone. | |||
Step by step guide: | |||
# Download an app for reading NFC information, such as [https://play.google.com/store/apps/details?id=com.nxp.taginfolite&hl=en_GB&gl=US NFC TagInfo by NXP]. | |||
# Open the app and go to 'Full Scan' tab. | |||
# Tap your card of choice on the back of the phone until a scan is complete. | |||
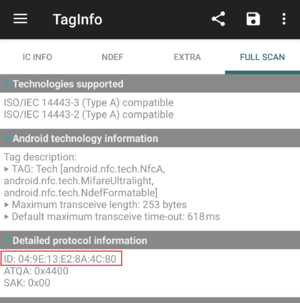
# Go back to 'full scan' tab and under detail protocol information section, find the ID reference and copy it. *See picture on the right [[File:TagInfo.png|thumb|right|View inside the app with card ID visible]] | |||
# Go to [https://london.hackspace.org.uk/members/addcard.php Add card section] on LHS website. To navigate to it go to Access -> Access Cards -> add a card by RFID unique id. | |||
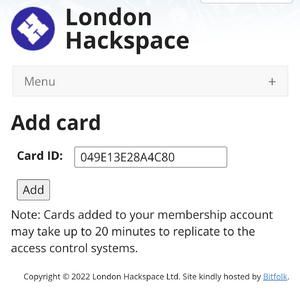
# Paste the ID reference into the field, remove all the semicolons and click add. *See picture on the right [[File:AddCardID.png|thumb|right|Field for adding the card ID onto the system]] | |||
# After about 20 minutes your card will work for accessing the space. | |||
=== Entering a working RFID into the membership database === | |||
Access is based on the RFID UID - the machine-readable serial number; it is not the number written on the back of your Oyster card. There are several ways to add a card: | |||
* Use the [[Membership Kiosk]] which is in the middle room next to the drinks fridge. You will need to enter your email address and password. If you use a password manager, and don't know your password, scan the QR code displayed on the kiosk. If your mobile device knows your login credentials, you can log in there. | |||
* If you have a [https://www.ebay.co.uk/sch/i.html?_nkw=ACR122U similar ACR122U card reader], you can get the code at [https://github.com/londonhackspace/Doorbot Github] and run <code>addcard.sh</code> on your own. If you have another reader that can give you the UID, log in to the website and add it at the [https://london.hackspace.org.uk/members/addcard.php Member Addcard webpage]. Note that our doorbot code is case sensitive; enter the (hex encoded) ID using without colons. | |||
* If you have an [https://en.wikipedia.org/wiki/List_of_NFC-enabled_mobile_devices Android phone that supports NFC], you can download one of the following free apps. Once you've downloaded and opened it, you'll be able to scan your RFID card and [https://london.hackspace.org.uk/members/addcard.php enter your card ID here.] Your phone may need to activate NFC connections/reading on your phone. On Android, you can find this in Config/Settings>Wireless and Network Connections. | |||
** [https://play.google.com/store/apps/details?id=com.nxp.taginfolite&hl=en_GB NFC TagInfo by NXP] (under Detailed Protocol Information, possibly removed in recent versions) | |||
** [https://play.google.com/store/apps/details?id=com.wakdev.wdnfc&hl=en_GB NFC Tools by wakdev] (under Serial number) | |||
'''Note that UID is entered in without colons. If your mobile NFC scanning application shows 04:2b:2e:6e:fa:bc:de <font color="red"> you should enter it into the website as 042b2e6efabcde </font>''' | |||
Do not worry if your card UID is shorter than the example - UIDs can be as short as 8 characters (4 hex pairs). | |||
There is the possibility for an integrated LHS membership RFID reader app - Hackspace member and former trustee [[User:JasperWallace|Jasper]] had built an Android app that automated the previous mobile task but the website changed and the app broke. If you're into mobile development and want to try to make something updated, please refer to the [https://pointless.net/~jasper/LHSSelfEnrole.apk LHS Self Enrol App] ([https://pointless.net/blog/2012/01/03/doorbot-app/ Background details and more info in the blog post from 2012]). | |||
==Doorbot sounds== | |||
Set your wave file (in wav or mp3 format) on the [https://london.hackspace.org.uk/members/cards.php members site]. The easiest way of doing this is to have a URL as the filename, and it will stream directly from that URL. | |||
Many early members enjoyed doorbot audio greetings in the style of [https://en.wikipedia.org/wiki/GLaDOS GLaDOS] - an artificial-intelligence sounding voice used in the Portal series of video games and in the movie Pacific Rim. Want to fit in with the 'classical' spirit of the Hackspace? Generate your own GLaDOS voice file on [http://glados.biringa.com/ this site here]. | |||
To avoid annoying people in the hackspace with overly long introduction sounds, the playback is limited to the first 17 seconds. | |||
=== Old GLaDOS Voice Generation Guide === | |||
(This doesn't work any more, the websites, and videos, that it refers to are no longer active) | |||
There was a guide on Youtube made to show the process as its hard to describe simply in text: [http://www.youtube.com/watch?v=OE8S9knXcW0 http://www.youtube.com/watch?v=OE8S9knXcW0] | |||
The original GLaDOS voices were generated by [[User:oni|oni]] following the method found by Tom Wyatt. To create a GLaDOS voice one must do the following: | |||
*Go to ATandT's Text to Speech Website (now offline). Type in your name and download the file. ''Alternately, use Cepstral or another online text-to-speech site allowing downloads.'' | |||
*Load up the program Melodyne | |||
*Select the entire Waveform | |||
*Using the '''melodic''' algorithm, double click on one section of the waveform. I believe this moves the form to its nearest notes. | |||
*Using the zig Zag looking tool, flatten the pitch. | |||
*Up the pitch by dragging upwards by 160 or so. | |||
*Save | |||
== Hardware == | == Hardware == | ||
Card readers are based around a pn532 chipset reader, configured to HSU (High Speed UART) mode. This should allow us to read the UID field from block zero of almost all 13.56MHz RFID cards,rings,bands,fobs. HOWEVER, some reader modules are better than others: | |||
* Elechouse V3 modules (genuine, red boards). Need a good +5V Vcc supply to be able to energise bank cards., use a DC/DC boost converter on long cable runs. | |||
* Deek-Robot modules (blue boards), beware the pinouts are incorrecly labelled on the silkscreen on one side of the board. These boards appear to no longer be manufactured. | |||
* Fake Elechouse V3 modules. Don't read very well at all except for very simple fobs with limited power draw. These can be identified by not having the word 'Elechouse' in italics, or having a full stop after the "NFC MODULE V3" label. | |||
Also on the reader modules, there's normally a pushbutton (for menu access on acnodes, or for doorbell action on the door readers), and an RGB LED. | |||
=== Front doorbot === | === Front doorbot === | ||
The front doorbot at 388 High Road is based on a TI Connected Launchpad, and works alongside the building landlord's door entry system. | The front doorbot at 388 High Road is based on a TI Connected Launchpad, and works alongside the building landlord's door entry system. During normal 'office hours', the maglock on the front door between the street and the shared lift lobby will be unlocked by the landlord's system. Only outside of normal hours will the door entry phone (only used by other tenants), and Hackspace's Front Doorbot will be necessary. Exit button is the landlord's door release button. | ||
The Hackspace card reader is a small blue enclosure on the right hand glass. The reader loop is at the top of the enclosure near the logo. | The Hackspace card reader is a small blue enclosure on the right hand glass. The reader loop is at the top of the enclosure near the logo. | ||
Front doorbot is in a shared enclosure with the Ground floor doorbot, and has a battery backup. In the event of power failure, it will still try to open doors with cached credentials, though some functions will depend on working networking and working acserver. | Front doorbot is in a shared enclosure with the Ground floor (aka Workshops) doorbot, and has a battery backup. In the event of power failure, it will still try to open doors with cached credentials, though some functions will depend on working networking and working acserver. | ||
The front doorbot sends out notifications using MQTT, to the topic base /door/gf-front-external. Any network device can listen in to these messages and set up their own bot/reporting infrastructure, etc. | The front doorbot sends out notifications using MQTT, to the topic base /door/gf-front-external. Any network device can listen in to these messages and set up their own bot/reporting infrastructure, etc. | ||
| Line 18: | Line 103: | ||
=== Back Doorbot === | === Back Doorbot === | ||
The back doorbot is the same as the front - with two differences: there's no bell, and the relay is activated by setting the pin state to HIGH. | The back doorbot is the same as the front - with two differences: there's no bell, and the relay is activated by setting the pin state to HIGH. | ||
=== Radio Lab Doorbot === | |||
The radio room is fitted with the same as the workshop door setup. The reader is a standard reader with a doorbell button, but there is currently no software to pick up on the button and make a noise, should there be a need for it. In the same enclosure as the Electronics Lab doorbot. SLA 12V backup battery. Restricted access. You need to have an amateur radio licence and have a facility induction to gain access. Contact [https://wiki.london.hackspace.org.uk/view/User:Marrold marrold] or [https://wiki.london.hackspace.org.uk/view/User:Tgreer tgreer]. Fitted with a reader with a doorbell button; though that doesn't do much yet. | |||
=== Biohackspace Doorbot === | === Biohackspace Doorbot === | ||
This is the same as above | This is the same as above. You need to be a member of the [[Biohacking|Biohackers]] to get in. Not currently deployed. | ||
=== 1st Floor Doorbot === | === 1st Floor Doorbot === | ||
Dual Solenoid bolt, 1st floor entrance from lift lobby. SLA 12V backup battery. ACNode shield v1. Node id 2 | |||
Rebuilt to make it more like the ground floor / front doorbot, and to implement a doorbell button on the reader. | |||
=== Back cage gate doorbot === | |||
Maglock on cage gate. Exit button in shrouded case. ACNode/Doorbot board. Doorbell button fitted in IP55 reader enclosure. Reader needs replacement with a more reliable module. Fitted with SD card for cacheing credentials. | |||
=== Maglock vs Solenoid latch vs Solenoid deadbolt === | |||
Though we currently use maglocks (because we had them in stock), we were aware of some issues with them, and have replaced some of them with solenoid deadbolts. The old Cisa solenoid latch on the back door required very gentle adjustments, and was not really suited to a double-leaf door installation. | |||
==Software== | |||
The source code for the software on the nodes is on [https://github.com/londonhackspace/acnode-cl Github], the server is here [https://github.com/londonhackspace/acserver-django acserver-django] | |||
All the logs go over the network to /var/log/network/ on [[adminstuff]], but it's not configured yet. | |||
The | The access list is JSON [http://github.com/londonhackspace/hackspace-foundation-sites/blob/master/london.hackspace.org.uk/carddb.php file]. | ||
Notification and status messages go via mqtt to the mqtt server. All the listener clients will subscribe to feeds on the mqtt server, and action notifications accordingly. | |||
The door opener sends an MQTT message whenever the door is opened by a member using their card <s>, or if the front doorbell is pushed</s>. | |||
=== Doorbot listener scripts === | |||
There are [http://github.com/londonhackspace/Doorbot/tree/master/listeners listeners] on [[mqtt]] that connect to '''mqtt''' to announce on IRC, and <s>flash the lights using '''Lighted'''</s>. By default, this will include your full real name. If you wish to change this behaviour, you can set up a nickname [https://london.hackspace.org.uk/members/cards.php in the cards section] of the member area. | |||
* [[Equipment/Holonyak|Holonyak]] and [[wilson]] runs listeners for the scrolling led boards | |||
* [[Hamming]] and [[Equipment/Holonyak|Holonyak]] do the audio announcements. | |||
The announcement listener uses the [http://en.wikipedia.org/wiki/GLaDOS GLaDOS] voice. You can generate and use your own file as a greeting. Update your 'Glados file' with a URL of an audio file, and it will play a maximum 12 seconds of the sample when you enter the 1st floor. File formats supported include mp3, m4a, wav, and non-DRM-protected aac. It will not play 'audio' from a YouTube URL. | |||
The Announcement listener runs on [[Hamming]], announcing the Workshops door, and on [[Holonyak]], announcing the back door, Workshops door, and cage door. | |||
The code that runs the [[Project:BandwidthMeter|bandwidth meter]] on [[adminstuff]] also listens for doorbell and member entry messages. | |||
== Managing Doorbots == | |||
=== Logging & maintenance === | |||
If you make changes or discover a problem with doorbot, please add it to '''[[Door control system/Logbook|the logbook]]'''. | |||
On [[hamming]], and [[Equipment/Holonyak|Holonyak]] the listeners are at /srv/doorbot/listeners | |||
sudo supervisorctl restart all | |||
== | === Emergency Exit door release === | ||
Next to all doors that act as emergency exits, and may need to be held open in the event of firefighters needing to retain access back into the building in the event of a fire, there are green 'break glass' style emergency exit buttons. Do not use these except in an emergency situation. You don't need to break the glass - which is actually plastic - but if they are triggered, then you will need a special key to reset them. The key is an orange plastic key, one of which is kept in the 1st Floor comms room doorbot enclosure, and the emergency exit button is reset by inserting the key into the underside of the emergency door release. | |||
All normal door exit buttons used in the hackspace are failsafe, that as well as signalling to the electronics to open the door (with a timed release), will also use another contact to break the circuit that would hold the door closed while the button is pressed. | |||
[[Category:Systems]] | [[Category:Systems]] | ||
[[Category:Infrastructure]] | [[Category:Infrastructure]] | ||
[[Category:Update Needed]] | |||
Latest revision as of 15:27, 5 November 2022
Preface
The major difference between a thing that might go wrong and a thing that cannot possibly go wrong is that when a thing that cannot possibly go wrong goes wrong it usually turns out to be impossible to get at or repair.
- Douglas Adams, 'Mostly Harmless'
Adding a card
If you're a new or pending member and looking to add a card to enter the space on your own, be sure you have an RFID or Contactless Smart Card that operates on the 13.56MHz frequency. You likely have several in your wallet and may not even know it. Note that our doorbot RFID readers do NOT read the older 125kHz frequency RFID cards frequently used for older 1990s/early 2000s era office/housing access, so not every card works in our system. You are likely in luck and have at least one 13.56MHz card already: the Transport for London Oyster card is by far the most popular card used by LHS members, but several members have also successfully used various hotel RFID keycards, contactless credit and debit cards, some RFID wristbands, and some compatible government ID cards as well.
Cards that are known to work well, in decreasing order of goodness
- Tesco Clubcard (full-sized credit-card form factor has RFID) - Free Sign-up
- EV charging membership cards (Source London, Polar, GeniePoint etc)
- BMW DriveNow membership cards
- Richmond Card for Parking Library Leisure Services in the London Borough of Richmond-upon-Thames - Free Sign-up for LBRUT residents
- Premier Inn keycards that you forgot to hand back on checkout.
- Transport for London Oyster cards - reports that some recent Oyster cards may draw more power for continuous reads.
Cards that don't work as well
- Contactless bank cards have more processing power on-board, and need quite a lot of RF energy to activate, so may not work as reliably as simpler cards like Oyster card or simple keyfobs. We have refitted all readers known to have problems activating bank cards with more reliable readers. Don't worry, we don't have the decryption keys to do anything banking related with your bank card, we just read the serial number, not the number printed on the front. (See below about Monzo and N26 payment cards, which have their own quirks)
- Passports with RFID chips will not work, and by attempting to use them will reset some internal read count in the passport, which may raise questions at border crossings.
- Some contactless bank cards are shipped to the recipient with the NFC functionality entirely disabled until the cardholder performs a valid chip-and-pin transaction.
- TO BE CLEAR, THESE KINDS OF CARDS ARE NOT RECOMMENDED. PLEASE DO NOT USE & PLEASE DO NOT COMPLAIN IF YOU EXPERIENCE ISSUES - ALL BETS ARE OFF ;)
'Cards' that don't work at all
- Apple Pay
- Android Pay
- Most Android card-simulator apps
- New (August 2019) Monzo payment cards
- The new "N26" Bank contactless card
All of these generate a random UID for each transaction.
- 125kHz frequency RFID cards (HID building entry systems)
If you still cannot find a capable card, you can buy them relatively easy off of eBay or Amazon UK or a local vendor such as Cool Components
Adding membership card remotely
A card can be linked to a membership account remotely, without going into the Hackspace. It's convenient for first-time access or in case you forget your card at home. Any of the cards listed in the section Cards that are known to work well should work. All you need is an NFC card reader, such as an Android phone. Step by step guide:
- Download an app for reading NFC information, such as NFC TagInfo by NXP.
- Open the app and go to 'Full Scan' tab.
- Tap your card of choice on the back of the phone until a scan is complete.
- Go back to 'full scan' tab and under detail protocol information section, find the ID reference and copy it. *See picture on the right
- Go to Add card section on LHS website. To navigate to it go to Access -> Access Cards -> add a card by RFID unique id.
- Paste the ID reference into the field, remove all the semicolons and click add. *See picture on the right
- After about 20 minutes your card will work for accessing the space.
Entering a working RFID into the membership database
Access is based on the RFID UID - the machine-readable serial number; it is not the number written on the back of your Oyster card. There are several ways to add a card:
- Use the Membership Kiosk which is in the middle room next to the drinks fridge. You will need to enter your email address and password. If you use a password manager, and don't know your password, scan the QR code displayed on the kiosk. If your mobile device knows your login credentials, you can log in there.
- If you have a similar ACR122U card reader, you can get the code at Github and run
addcard.shon your own. If you have another reader that can give you the UID, log in to the website and add it at the Member Addcard webpage. Note that our doorbot code is case sensitive; enter the (hex encoded) ID using without colons. - If you have an Android phone that supports NFC, you can download one of the following free apps. Once you've downloaded and opened it, you'll be able to scan your RFID card and enter your card ID here. Your phone may need to activate NFC connections/reading on your phone. On Android, you can find this in Config/Settings>Wireless and Network Connections.
- NFC TagInfo by NXP (under Detailed Protocol Information, possibly removed in recent versions)
- NFC Tools by wakdev (under Serial number)
Note that UID is entered in without colons. If your mobile NFC scanning application shows 04:2b:2e:6e:fa:bc:de you should enter it into the website as 042b2e6efabcde
Do not worry if your card UID is shorter than the example - UIDs can be as short as 8 characters (4 hex pairs).
There is the possibility for an integrated LHS membership RFID reader app - Hackspace member and former trustee Jasper had built an Android app that automated the previous mobile task but the website changed and the app broke. If you're into mobile development and want to try to make something updated, please refer to the LHS Self Enrol App (Background details and more info in the blog post from 2012).
Doorbot sounds
Set your wave file (in wav or mp3 format) on the members site. The easiest way of doing this is to have a URL as the filename, and it will stream directly from that URL.
Many early members enjoyed doorbot audio greetings in the style of GLaDOS - an artificial-intelligence sounding voice used in the Portal series of video games and in the movie Pacific Rim. Want to fit in with the 'classical' spirit of the Hackspace? Generate your own GLaDOS voice file on this site here.
To avoid annoying people in the hackspace with overly long introduction sounds, the playback is limited to the first 17 seconds.
Old GLaDOS Voice Generation Guide
(This doesn't work any more, the websites, and videos, that it refers to are no longer active) There was a guide on Youtube made to show the process as its hard to describe simply in text: http://www.youtube.com/watch?v=OE8S9knXcW0
The original GLaDOS voices were generated by oni following the method found by Tom Wyatt. To create a GLaDOS voice one must do the following:
- Go to ATandT's Text to Speech Website (now offline). Type in your name and download the file. Alternately, use Cepstral or another online text-to-speech site allowing downloads.
- Load up the program Melodyne
- Select the entire Waveform
- Using the melodic algorithm, double click on one section of the waveform. I believe this moves the form to its nearest notes.
- Using the zig Zag looking tool, flatten the pitch.
- Up the pitch by dragging upwards by 160 or so.
- Save
Hardware
Card readers are based around a pn532 chipset reader, configured to HSU (High Speed UART) mode. This should allow us to read the UID field from block zero of almost all 13.56MHz RFID cards,rings,bands,fobs. HOWEVER, some reader modules are better than others:
- Elechouse V3 modules (genuine, red boards). Need a good +5V Vcc supply to be able to energise bank cards., use a DC/DC boost converter on long cable runs.
- Deek-Robot modules (blue boards), beware the pinouts are incorrecly labelled on the silkscreen on one side of the board. These boards appear to no longer be manufactured.
- Fake Elechouse V3 modules. Don't read very well at all except for very simple fobs with limited power draw. These can be identified by not having the word 'Elechouse' in italics, or having a full stop after the "NFC MODULE V3" label.
Also on the reader modules, there's normally a pushbutton (for menu access on acnodes, or for doorbell action on the door readers), and an RGB LED.
Front doorbot
The front doorbot at 388 High Road is based on a TI Connected Launchpad, and works alongside the building landlord's door entry system. During normal 'office hours', the maglock on the front door between the street and the shared lift lobby will be unlocked by the landlord's system. Only outside of normal hours will the door entry phone (only used by other tenants), and Hackspace's Front Doorbot will be necessary. Exit button is the landlord's door release button.
The Hackspace card reader is a small blue enclosure on the right hand glass. The reader loop is at the top of the enclosure near the logo.
Front doorbot is in a shared enclosure with the Ground floor (aka Workshops) doorbot, and has a battery backup. In the event of power failure, it will still try to open doors with cached credentials, though some functions will depend on working networking and working acserver.
The front doorbot sends out notifications using MQTT, to the topic base /door/gf-front-external. Any network device can listen in to these messages and set up their own bot/reporting infrastructure, etc.
Back Doorbot
The back doorbot is the same as the front - with two differences: there's no bell, and the relay is activated by setting the pin state to HIGH.
Radio Lab Doorbot
The radio room is fitted with the same as the workshop door setup. The reader is a standard reader with a doorbell button, but there is currently no software to pick up on the button and make a noise, should there be a need for it. In the same enclosure as the Electronics Lab doorbot. SLA 12V backup battery. Restricted access. You need to have an amateur radio licence and have a facility induction to gain access. Contact marrold or tgreer. Fitted with a reader with a doorbell button; though that doesn't do much yet.
Biohackspace Doorbot
This is the same as above. You need to be a member of the Biohackers to get in. Not currently deployed.
1st Floor Doorbot
Dual Solenoid bolt, 1st floor entrance from lift lobby. SLA 12V backup battery. ACNode shield v1. Node id 2
Rebuilt to make it more like the ground floor / front doorbot, and to implement a doorbell button on the reader.
Back cage gate doorbot
Maglock on cage gate. Exit button in shrouded case. ACNode/Doorbot board. Doorbell button fitted in IP55 reader enclosure. Reader needs replacement with a more reliable module. Fitted with SD card for cacheing credentials.
Maglock vs Solenoid latch vs Solenoid deadbolt
Though we currently use maglocks (because we had them in stock), we were aware of some issues with them, and have replaced some of them with solenoid deadbolts. The old Cisa solenoid latch on the back door required very gentle adjustments, and was not really suited to a double-leaf door installation.
Software
The source code for the software on the nodes is on Github, the server is here acserver-django
All the logs go over the network to /var/log/network/ on adminstuff, but it's not configured yet.
The access list is JSON file.
Notification and status messages go via mqtt to the mqtt server. All the listener clients will subscribe to feeds on the mqtt server, and action notifications accordingly.
The door opener sends an MQTT message whenever the door is opened by a member using their card , or if the front doorbell is pushed.
Doorbot listener scripts
There are listeners on mqtt that connect to mqtt to announce on IRC, and flash the lights using Lighted. By default, this will include your full real name. If you wish to change this behaviour, you can set up a nickname in the cards section of the member area.
- Holonyak and wilson runs listeners for the scrolling led boards
- Hamming and Holonyak do the audio announcements.
The announcement listener uses the GLaDOS voice. You can generate and use your own file as a greeting. Update your 'Glados file' with a URL of an audio file, and it will play a maximum 12 seconds of the sample when you enter the 1st floor. File formats supported include mp3, m4a, wav, and non-DRM-protected aac. It will not play 'audio' from a YouTube URL. The Announcement listener runs on Hamming, announcing the Workshops door, and on Holonyak, announcing the back door, Workshops door, and cage door.
The code that runs the bandwidth meter on adminstuff also listens for doorbell and member entry messages.
Managing Doorbots
Logging & maintenance
If you make changes or discover a problem with doorbot, please add it to the logbook.
On hamming, and Holonyak the listeners are at /srv/doorbot/listeners
sudo supervisorctl restart all
Emergency Exit door release
Next to all doors that act as emergency exits, and may need to be held open in the event of firefighters needing to retain access back into the building in the event of a fire, there are green 'break glass' style emergency exit buttons. Do not use these except in an emergency situation. You don't need to break the glass - which is actually plastic - but if they are triggered, then you will need a special key to reset them. The key is an orange plastic key, one of which is kept in the 1st Floor comms room doorbot enclosure, and the emergency exit button is reset by inserting the key into the underside of the emergency door release.
All normal door exit buttons used in the hackspace are failsafe, that as well as signalling to the electronics to open the door (with a timed release), will also use another contact to break the circuit that would hold the door closed while the button is pressed.